To protect your data and that of your customers, IT security is no longer an option, but an imperative necessity. Faced with the constant evolution of cybermenaces, how to strengthen your software, tools and computer networks? Thanks to the One Time Password!
Are you wondering about the security of your business? Consider using a cybersecurity consultant on Coder.com.
One Time Passwords add robust protection to your IT equipment. Discover their functioning and importance in securing your business …
What is a One Time Password?
You have probably already used a One Time Password (OTP) without knowing it.
An OTP, sent by SMS, email or via an application, is a single -use password that adds an additional protection layer. Its dynamic nature means that it changes after each use, making any future interceptor helpless.
The usual and reused passwords, are often reused, are real magnets for hackers. The OTP, on the other hand, serves as a second defense bulwark, a reliable ally in addition to your traditional password.
For flawless security, OTPs rest on solid safety standards:
- Totp (Time-Based One-Time Password) : Create an OTP valid for a short time, generally between 30 and 60 seconds.
- Hotp (Hmac-Based One-Time Password) : Uses an evolutionary counter for the generation of each new OTP.
These standards transform the One Time Passwords into an ideal solution for two -factor authentication
How does a One Time Password work?
There are several methods to generate a One Time Password.
The most widespread method is based on time: here, the OTP is generated by combining the current time with a secret key, shared between the user and the online service. Each 30 to 60 seconds, a new OTP is created according to a specific algorithm. Applications such as Google Authenticator and Authy use this technique to secure access to various online services.
Another method, based on a counter, uses the number of interactions between the user and the service to generate a unique OTP in each new operation. This approach is frequently adopted by physical devices such as secure USB keys or smart cards, where the secret key and the counter are saved.
Finally, the challenge method creates the OTP following a specific question posed by the online service. This question can be random or based on personal information, thus guaranteeing that the OTP is unique to each new request. Services like Paypal or Amazon employ this solution.
Who are the OTPs for?
The OTPs are as much intended for the internal computer park of a company, as to customers.
The use of OTP internally
One Time Passwords (OTP) transform the way companies secure their internal environment. Easy to use, they offer employees a safe connection method, freeing them from the burden of retaining multiple passwords.
This simplicity results in increased productivity and reinforced protection of sensitive data, which range from information to employees to commercial transactions, including patents and marketing documents.
Using OTP Customers
On the customer side, OTPs are the key to a safer and fluid online experience. Used by online e-commerce and services, they guarantee the security of customer data while simplifying the verification processes.
Result: improved user experience and reinforced confidence.


Why should companies adopt the One Time Password?
OTPs offer several significant advantages:
- Reinforced security : They considerably reduce the risk of hacking of accounts, whether internally or those of your customers.
- Ease of integration : They can be easily integrated into existing systems. A Cybersecurity provider will be able to support you during this procedure.
- Increased confidence of customers : Using OTP shows that your business takes data protection seriously. This encourages customers to choose you as a trusted partner.
- More fluid connection : the abandonments of purchase due to the oblivion of passwords are thus minimized.
How to choose an OTP generator?
When selecting an OTP supplier for your business, consider these key factors:
- End -to -end safety : Opt for a reliable supplier offering robust encryption and automation options for double authentication (2FA).
- Ease of installation : Choose a supplier whose API is easily integrated into your existing systems, with clear documentation.
- Profitability : Look for economic options with personalized plans or volume discounts, while checking the absence of hidden costs.
- Customer service : Favor suppliers offering 24/7 customer support via email, cat and telephone.
3 OTP generators to know
If you want to use a One Time Password to secure your IT tools, here are 3 powerful OTP solutions:
1. Google Authenticator: the simplest OTP solution
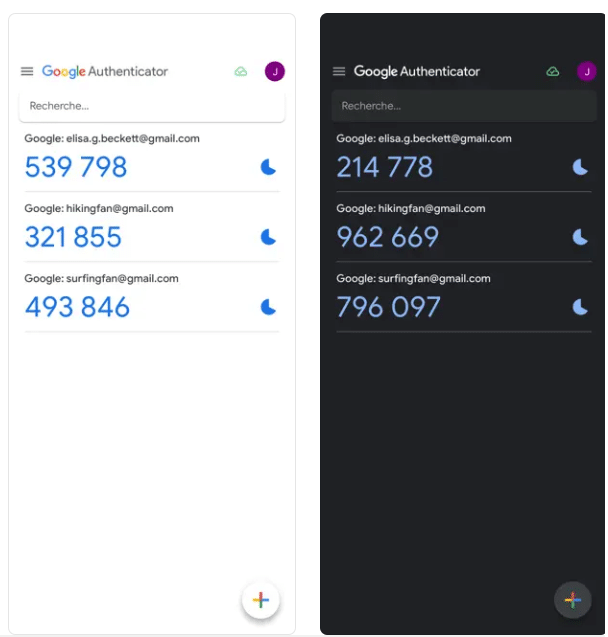

Free and intuitive tool, Google Authenticator offers robust multi-factor authentication on Android, iOS and many other platforms. It generates otp of six to eight digits which are renewed every 30 seconds.
Easy to use, it nevertheless requires an individual configuration for each site and remains vulnerable to attacks if the smartphone is compromised.
2. Onelogin Protect: OTP authentication software
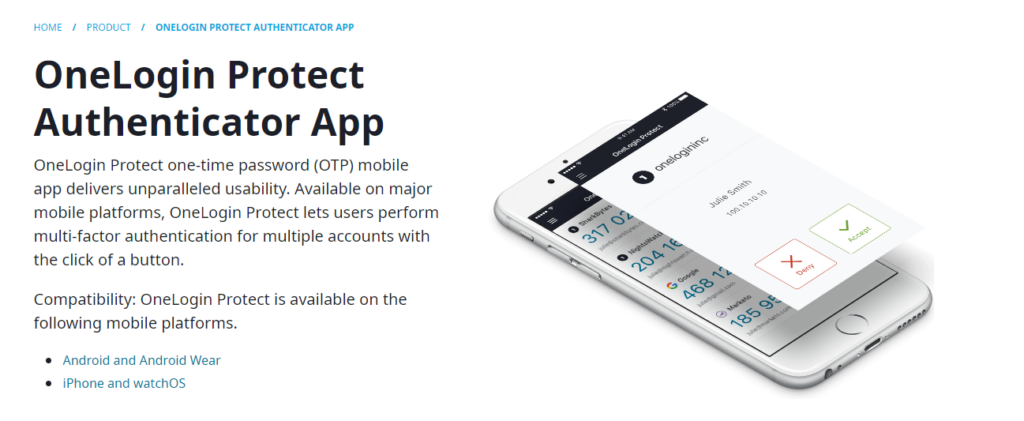

Using a Totp algorithm, Onelogin Protect Allows you to implement multi-factory authentication. This mobile application generates valid passwords for 30 seconds.
Easy to install and configure, it requires internet connection and can be less practical if the smartphone is lost or stolen.
3. Authy: an ideal one time password for 2 factors authentication

Authy is a free two -factor authentication solution, easy to configure and equipped with features like Touch ID or encrypted backups. The platform prevents accounting of accounts in the event of loss of the phone and synchronizing authentication on various devices intuitively.
Our tip for using One Time Password in your business
The adoption of One Time Passwords in your business is a strategic step towards enhanced security.
A key tip to optimally use OTP is to educate and train your staff! Each employee must know the importance and operation of this system to use it on a daily basis, and guide your customers during their connection step.
For the implementation of a tailor -made cybersecurity strategy, call on a freelance Cybersecurity expert on Coder.com!
